寄存器相关知识笔记
X86-64 Register
Simple Demo 1
|
|
GDB Disassemble Output
|
|
注意到
|
|
使用了%edi,%rsi,%rcx,%rax,查阅手册
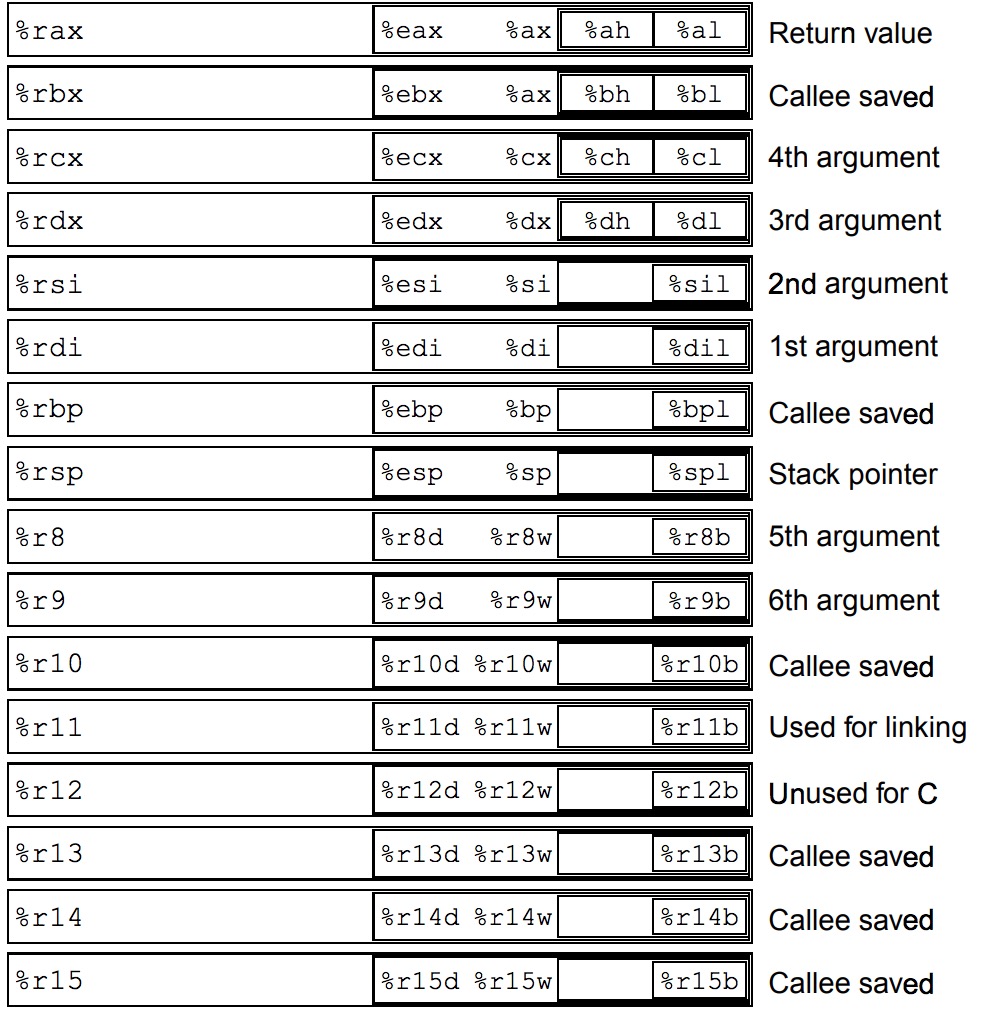
Simple Demo2
|
|
如果在MacOS系统想要进行Buffer Overflow的测试的话,如果使用GCC编译需要用这两个-fno-stack-protector -D_FORTIFY_SOURCE=0选项。
GCC堆栈保护
-fstack-protector:
启用堆栈保护,不过只为局部变量中含有 char 数组的函数插入保护代码。
-fstack-protector-all:
启用堆栈保护,为所有函数插入保护代码。
-fno-stack-protector:
禁用堆栈保护。
stack-protector保护方式修改函数栈的组织,在缓冲区和可控数据buffer间插入一个canary word(标志)。当缓冲区被溢出时,canary word 会首先被覆盖。通过检查 canary word 的值是否被修改,就可以判断是否发生了溢出。
汇编代码中mov %edi,-0x8(%rbp)这样的为AT&T的语法。
Intel 语法的间接内存引用的格式为:
section:[base+index*scale+displacement]
而在 AT&T 语法中对应的形式为:
section:displacement(base,index,scale)
mov %edi,-0x8(%rbp) =(%rbp + 0*0 - 0x8)